Search results for tag #network
@abbas_dp Learnt new things from #Protest #Apps #Delta #Privacy #Culture #Party !
1☑️ Delta Chat can be installed on a #TAILS OS USB thumb-drive 💾 as a Persistent app + used via #TOR #Network
2☑️ The #Persian / #Iranian calendar is #observation-based, unlike the #Gregorian calendar, which is #rule-based !
( lol there exists other calendars in the world and ways! 🌜 🌚 📆 🌔 🌛
https://en.wikipedia.org/wiki/Iranian_calendars )
3☑️ ...a record of 500 active #DeltaChat servers during #Iran's internet #blackout period
So today i had a reunion with a fu*ker from an US company that sell network hardware that rime with Frisco.
Long story short, he was entitled as hell when arriving, and was shocked when i anounced him that we would not buy any hardware or service from them, that they where on our blacklist AND that we started to purge their existing hardware.
Now "Frisco" know Orange pedo can cost them a contract in million for both hardware renewal and service.
Tiens depuis ce matin j'ai un comportement spécial sur le TorBrowser, après avoir ouvert plusieurs onglets en succession rapide : y'en a aucun qui se charge, et l'onglet "réseau" de l'inspecteur me dit "aucune requête" quand je tente de recharger une page ou d'en ouvrir un autre...
#TorBrowser #Firefox #Network et peut-être #PEBKAC ?
In this demo, see how to use Visual Studio Code, GitHub Copilot, and the Puppet MCP Server to generate an EdgeOps automation task for your network devices!
This video shows you how to setup your mcp.json file and then prompt for a task that configures NTP servers on a switch using your device's configuration info.
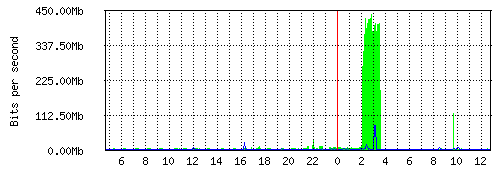
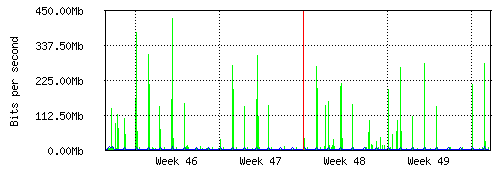
My router interface traffic graphs are pretty useless. Every night around 2:00am, various things run backups. Some do backups across the network, others copy out to an off-site location. But the bottom line is that if I look at my network interface graphs, that massive spike every night ruins the Y axis.
These are the daily, weekly, and monthly graphs. And the fact that daily hits around 450M, but ordinary hours are like 8-10M, it means I can't see the rest of the graph. It means that I can't spot changes or interesting things.
I'm not really sure how to do better. (It's amateur hour over here)
#Montag – morgens voller Energie und Elan den PC starten, um dann schockiert auf den #tty Login-Prompt, statt das #ly Anmeldefenster zu starren. Dann findet sich in der #systemctl-Liste weder ein ly-Dienst noch #network-Service. Ja, ich hatte am Freitag noch eine Systemaktualisierung durchgeführt. Da war weder ungewöhnliches noch verdächtiges dabei und lief fehlerfrei durch. Nun existiert das Kommando #startx angeblich nicht mehr.
Auf welchem Stockwerk sich meine Laune befindet, dürfte leicht zu erraten sein 🤬 Nein, ich habe keine Motivation zur Fehlersuche. Mir hängen solche Sperenzien zum Hals heraus 🤯 Früher fand ich sowas spannend, weil es mich von wichtigen Dingen ablenkte. Doch diese Zeiten sind vorbei, ich will einfach nur ungestört arbeiten. Vielleicht wechsel ich doch wieder von #ArchLinux zu #Debian. Wenn "rolling" mir immer wieder das System zerschießt, kann ich darauf verzichten. #Linux
We’ve published new research from the EU co-funded project NGSOTI: “Learning from large-scale IPv4 blackhole: Behavioral analysis of SNMP traffic”.
Over a 12-month period (Nov 2024–Oct 2025), our network telescope captured ~634 million unsolicited SNMP queries from more than 153,000 unique IPv4 sources scanning an unused /18 block.
The origins of the traffic are globally distributed, with notable concentrations from Indonesia, China, the United States, Germany, Chile and others, as well as a few outliers generating unusually high volumes. A significant portion of the scanning activity can also be attributed to infrastructure belonging to commercial threat-intelligence and scanning companies, providing useful context on what constitutes “expected” background noise.
The analysis covers SNMP version usage (v1/v2c overwhelmingly dominant, minimal v3), community-string patterns (default, weak, and undocumented strings), and OIDs that point to which device vendors are most scanned.
This dataset provides insight into real-world reconnaissance trends targeting SNMP-capable infrastructure, helping defenders better understand background noise and scanning behaviours.
🔗 Full report: https://d4-project.org/2025/11/27/Learning-from-Large-Scale-IPv4-blackhole-behavioral-analysis-of-SNMP-traffic.html
🔗 PDF version: https://d4-project.org/assets/behavioral-analysis-of-snmp-traffic.pdf
Co-funded by European Cybersecurity Competence Centre (ECCC) under the NGSOTI project.
#cybersecurity #networkanalysis #cybersecurity #snmp #network #internet #dfir
Für diesen Artikel muss man sich Zeit nehmen 😜
heise+ | Wie man einen #Raspi als #OpenWrt-Router für mehrere Netze konfiguriert | c't Magazin https://www.heise.de/ratgeber/Wie-man-einen-Raspi-als-OpenWrt-Router-fuer-mehrere-Netze-konfiguriert-10751111.html #heiseplus #Linux  #RaspberryPi #VLAN #Netzwerk #network
#RaspberryPi #VLAN #Netzwerk #network
So, I discovered that it's customary to give an #introduction on #mastodon so here I am.
I'm @shalien , a computer enthusiast as #dev as #network .
Disappointed with Twitter / X , I resurrected my #mastodon instance and here I am.
I hope to discover something else, something healthier and more relaxing than the permanent chaos of Twitter.
Looking forward to seeing you in the #Fediverse!
The Banana Pi BPI-R4 Pro is a new Router Board based on MediaTek MT7988A SoC (quad-core Arm Corex-A73 processor), 2x 10GbE SFP+, 2x 10GbE RJ45, 4x 2.5 Gbps Ethernet RJ45 ports, 8 GB RAM, 2x M.2 sockets for NVMe SSD #Network #Hardware https://www.cnx-software.com/2025/10/20/banana-pi-bpi-r4-pro-board-offers-2x-10gbe-sfp-cages-6x-10gbe-2-5gbe-gbe-ports-wifi-7-support/
Is anyone else finding that their network connections are VERY slow this week? I'm trying to decide whether the slowness and browser timeouts are still the aftermath of the big outage (so likely to improve) or an effect of my awful internet connection (so I need to yell at someone at my ISP.
DNS is probably involved, since the worst problems seem to happen when I try to follow links to servers I'm not currently accessing.
Does anyone have root DNS servers they favor?
Traffic meter per ASN without logs https://anarc.at/blog/2025-05-30-asncounter #debian-planet #python-planet #software #network #sysadmin #tor #censorship #python
🚀 Mettre en place un DNS Failover avec MikroTik
Vous voulez améliorer la résilience de votre réseau ? Dans cet article, je vous montre comment faire du DNS Failover avec MikroTik et containerlab.
➡️ https://blog.jesuislibre.org/homelab-dns-failover-episode-3/

 Shalien
Shalien
 🇸🇪
🇸🇪![[?]](https://social.dk-libre.fr/social/oldsysops/s/7e93fa6bf16b47da4f57ddf9072aff8c.png)

